Researchers identify ‘security flaws’ in contact tracing app
They have passed their findings to the National Cyber Security Centre, which is involved in the app’s development.

Security researchers have highlighted a number of potential flaws in the coronavirus contact tracing app.
The issues have been flagged to the National Cyber Security Centre (NCSC), which is involved in the app’s development, and it said it is in the process of fixing them.
The researchers also warned legal protections around data use are needed in order to better protect personal privacy on the app, which is currently being trialled on the Isle of Wight.
They say data associated with the app should be protected by legislation “from use by law enforcement, or any usage not directly related to Covid-19 prevention”.
Harriet Harman, chair of the Joint Committee on Human Rights, said on Tuesday that new laws to protect the privacy of personal information gathered by the app are a “no brainer”.
Ms Harman, who has prepared a Bill on the issue which is ready for introduction, said assurances by Health Secretary Matt Hancock do not provide any protection after he wrote to her saying the Government believes legislation is unnecessary because there is already the Data Protection Act.
In their study of the contact tracing app, which was shared with the NCSC last week, security researchers Professor Vanessa Teague and Dr Chris Culnane identified a number of issues, including a weakness in the app’s registration process which could be exploited by hackers and used to manipulate data or create logs of fake contact events.
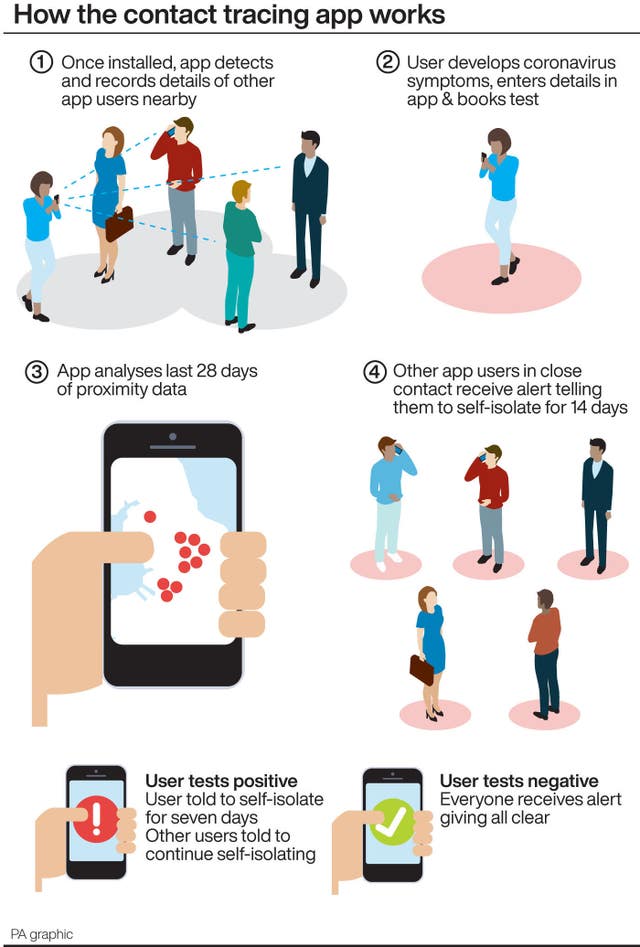
It also highlighted a flaw which means storing unencrypted data on a user’s phone could potentially be used by law enforcement agencies to determine when two or more people met.
The research added that generating new random ID codes for users once a day, rather than every 15 minutes like in other systems, makes it theoretically possible to determine intimate details about an app user’s lifestyle, such as whether they “woke up and went to bed with the same person, or more revealingly, if they did not”.
Dr Ian Levy, technical director of the NCSC, thanked the researchers and confirmed the app development team is addressing all the issues raised.
“The intent of being open before national launch was to show what the app will do, how it will do it, and to get some peer review from security and privacy researchers,” he wrote in a blog post.
“Thank-you to everyone who’s taken the time to look at the design and the beta code and provide us with useful feedback, whether that’s directly, on GitHub or through the NCSC’s vulnerability disclosure programme.
“Everything reported to the team will be properly triaged (although this is taking longer than normal).”
Dr Levy added the NCSC would not comment on specific legal issues raised by the researchers.
In a further statement, a spokesman for the NCSC said: “Responsible security researchers are an overwhelming force for good and their feedback was openly requested for the quickly developed beta app.
“It was always hoped that measures such as releasing the code and explaining decisions behind the app would generate meaningful discussion with the security and privacy community.
“We look forward to continuing to work with security and cryptography researchers to make the app the best it can be for the public.”





